Hi, Readers.
The preview environment for Dynamics 365 Business Central 2022 release wave 2 (BC21) is available. Learn more: Link.
I will continue to test and share some new features that I hope will be helpful.
Apply resource exposure policy to DEV extensions:
Business value:
When developing and deploying AL extensions from Visual Studio Code, the extensions are deployed to sandboxes as DEV extensions. Until now, these have been debuggable. Sometimes this might not be desirable—for example, when deploying only for test purposes in a sandbox environment shared by multiple partners. To address this, we have extended the resource exposure policy for extensions with the ability to override the default DEV handling and enforce the resource exposure policy for the DEV extension as well.
https://docs.microsoft.com/en-us/dynamics365-release-plan/2022wave2/smb/dynamics365-business-central/apply-resource-exposure-policy-dev-extensions
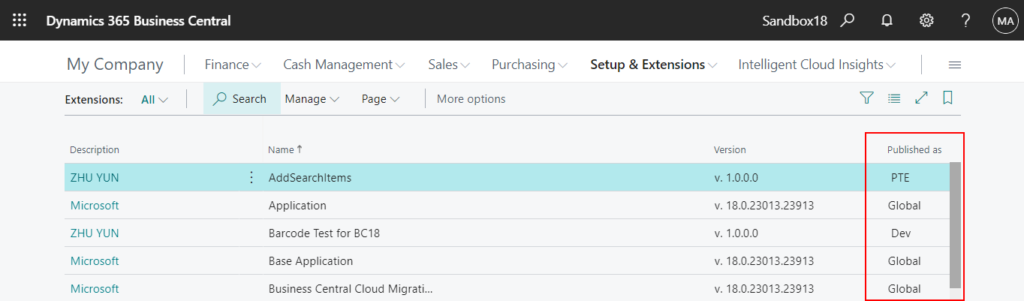
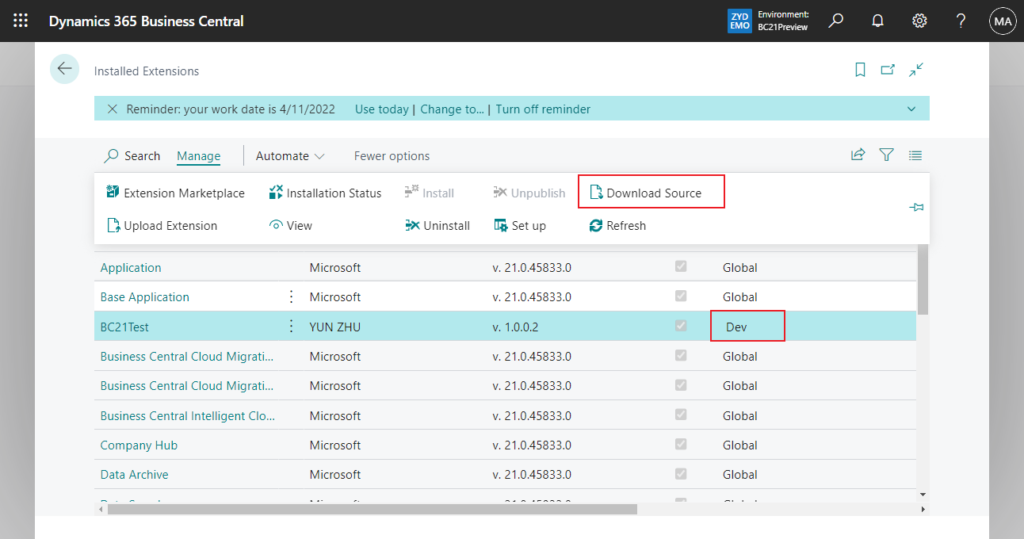
In Dynamics 365 Business Central 2021 release wave 1 (BC18), Microsoft added the scope of extensions (Global, PTE, Dev) to the Extension management page. More details: The scope of extensions (Global, PTE, Dev)
- Global (Global Scope): AppSource Extensions (Including Microsoft standard extensions)
- PTE (Tenant Scope): PTEs published by Upload Extension on the Extension Management page.
- Dev (Development Scope): PTEs published by VS Code.
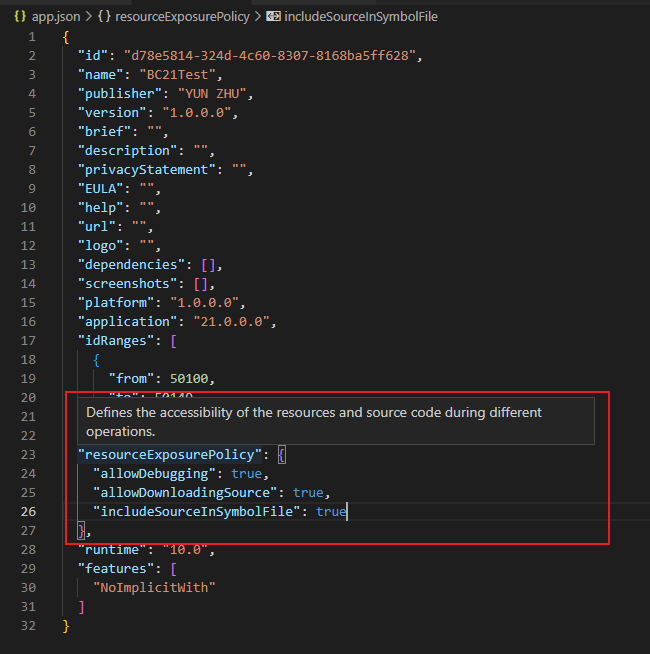
And in Business Central 2021 wave 2 (BC19), Microsoft has brought us a new feature, Richer access control for extension source in cloud environments (‘showMyCode’ -> ‘resourceExposurePolicy’).
“resourceExposurePolicy”: Defines the accessibility of the resources and source code during different operations. (Used to replace the ‘showMyCode‘ setting)
But there has always been a problem with this. If you are publishing the extension from the VS code (DEV), the resourceExposurePolicy setting will not work.
For example, Disabling “Download Source” action in Extension management. – Dynamics 365 Business Central Forum Community Forum
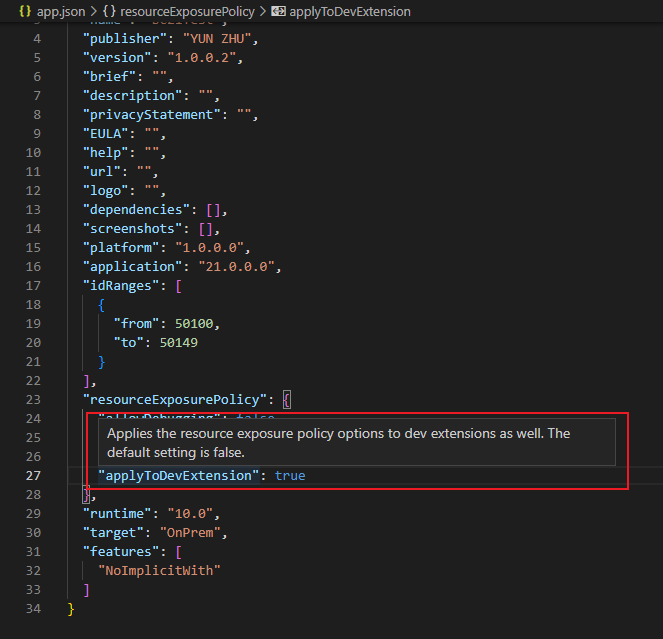
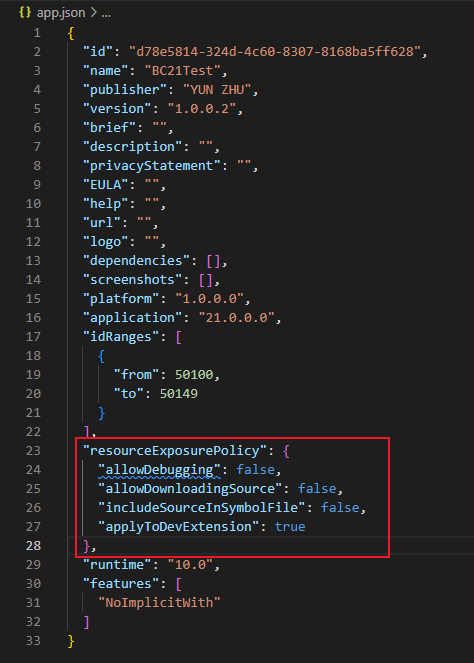
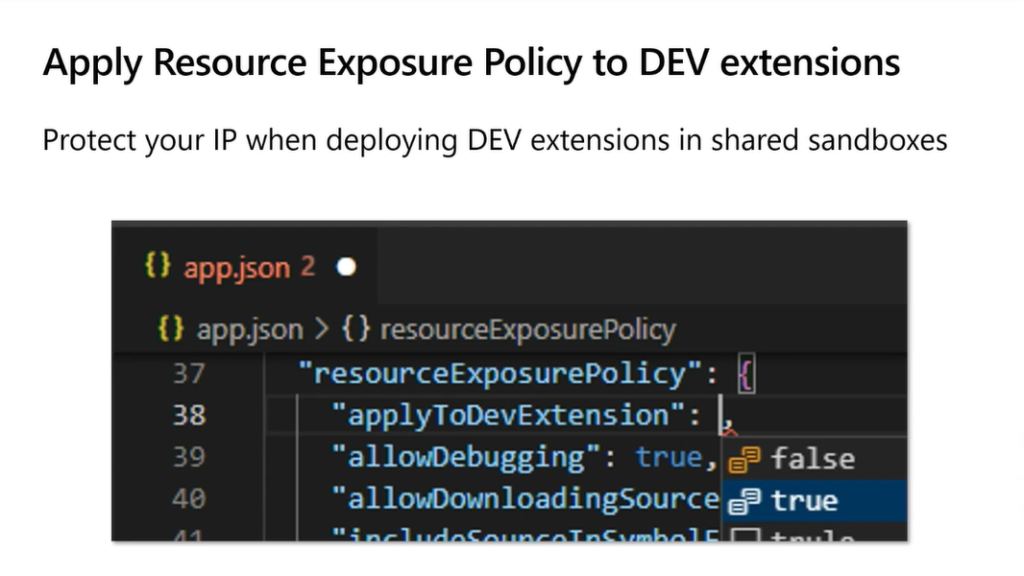
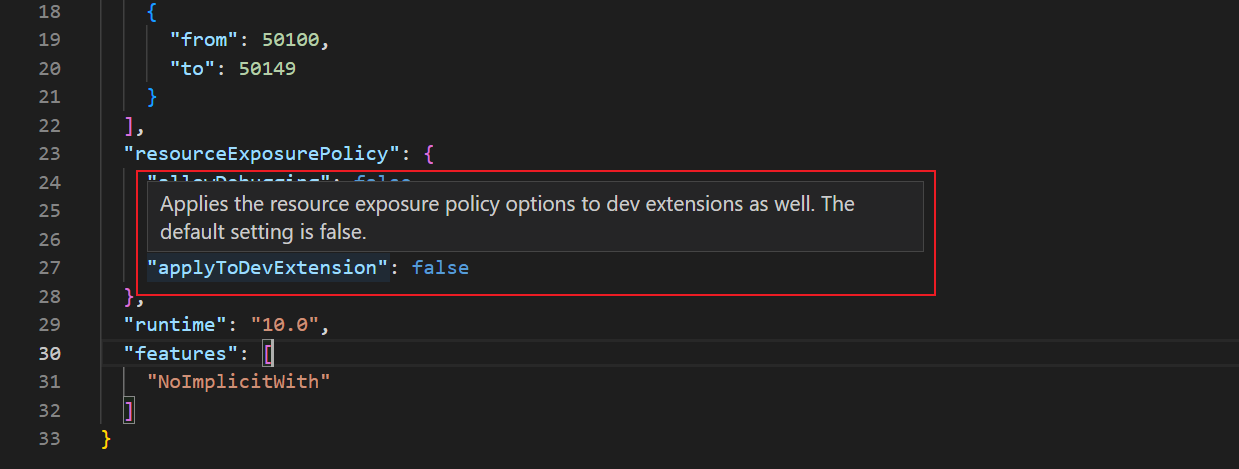
Now, the resourceExposurePolicy property in the app.json file now contains a new “applicableToDevExtension” flag.
“applyToDevExtension”: Applies the resource exposure policy options to dev extensions as well. The default setting is false.
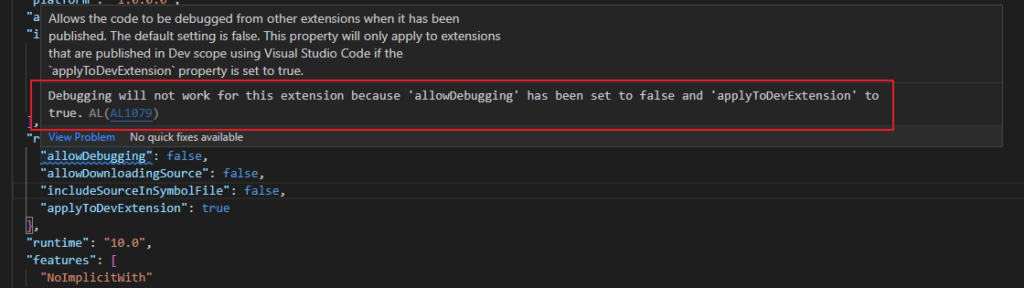
With this update, the instructions for “allowDebugging” and “includeSourceInSymbolFile” have also be updated.
“allowDebugging”: Allows the code to be debugged from other extensions when it has been published. The default setting is false. This property will only apply to extensions that are published in Dev scope using Visual Studio Code if the `applyToDevExtension` property is set to true.
“includeSourceInSymbolFile”: Includes the source code and all other resources that were part of the extension package at the time it was published, in the symbol package. The default setting is false. This property will only apply to extensions that are published in Dev scope using Visual Studio Code if the `applyToDevExtension` property is set to true.
So if this flag is set to true, the other resource exposure flags will be applied when deploying the extension from Visual Studio Code as a DEV extension. This allows, for example, blocking debugging DEV extensions.
Another example:
The effective policies for this package do not allow you to download the source code. Contact the extension provider for more information.

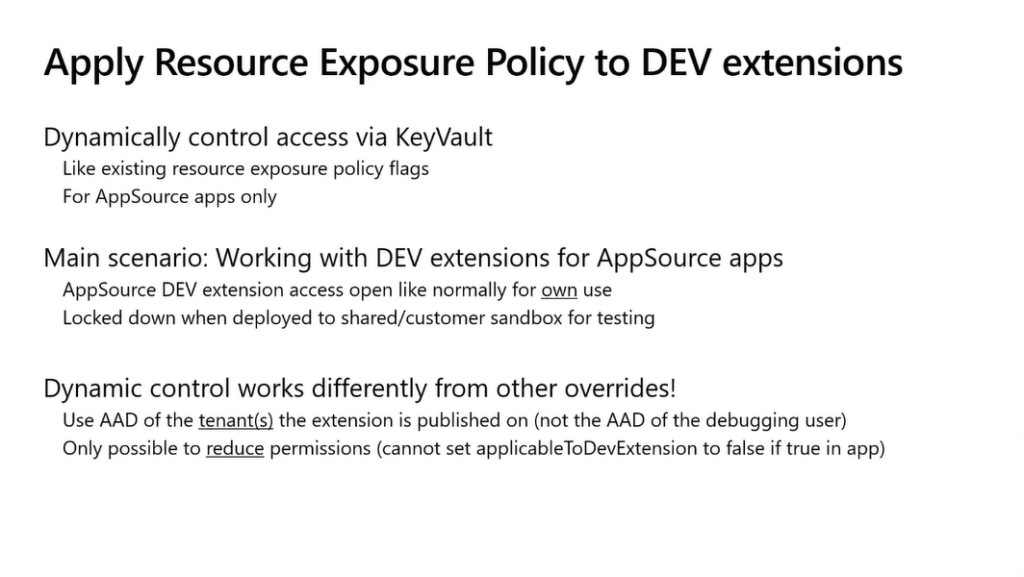
As with the other resource exposure policy options, you can also control access dynamically via an Azure Key Vault secret for resource exposure policy. Here you set the “applicableToDevExtension” flag to the tenant environment Azure Active Directory (Azure AD) where the resource exposure policy will be applied to the DEV extension (not the Azure AD of the debugging user).
More details: Using App Key Vaults with Business Central Extensions
Note:
For Business Central online, the app key vault feature is only supported for AppSource extensions.
Because this setting is additive, you can dynamically enforce it for select environments if it’s not enforced in the app.json file settings, but you can’t turn it off (that is, allow debugging) for select environments if it’s enforced by the app.json file settings. You can only dynamically reduce resource exposure.
PS:
1. Resource exposure policies, including that mentioned here, are not applied on-premises.
2. Another new feature about resource exposure policy in Business Central 2022 wave 2 (BC21)
Resource exposure policies for apps are on by default (“allowDebugging”: true, “allowDownloadingSource”: true, “includeSourceInSymbolFile”: true)
Give it a try!!!😁
Update from Business Central Launch Event (2022 release wave 2)
END
Hope this will help.
Thanks for reading.
ZHU

コメント