Hi, Readers.
Dynamics 365 Business Central 2023 wave 1 (BC22) is generally available this month. More details: Dynamics 365 Business Central 2023 release wave 1 (BC22)
I will continue to test and share some new features that I hope will be helpful.
This new feature is not mentioned in the 2023 wave1 release plan, but it is in Business Central Launch Event (2023 release wave 1) and AL Language extension changelog version 11.0.
Inherent Permissions
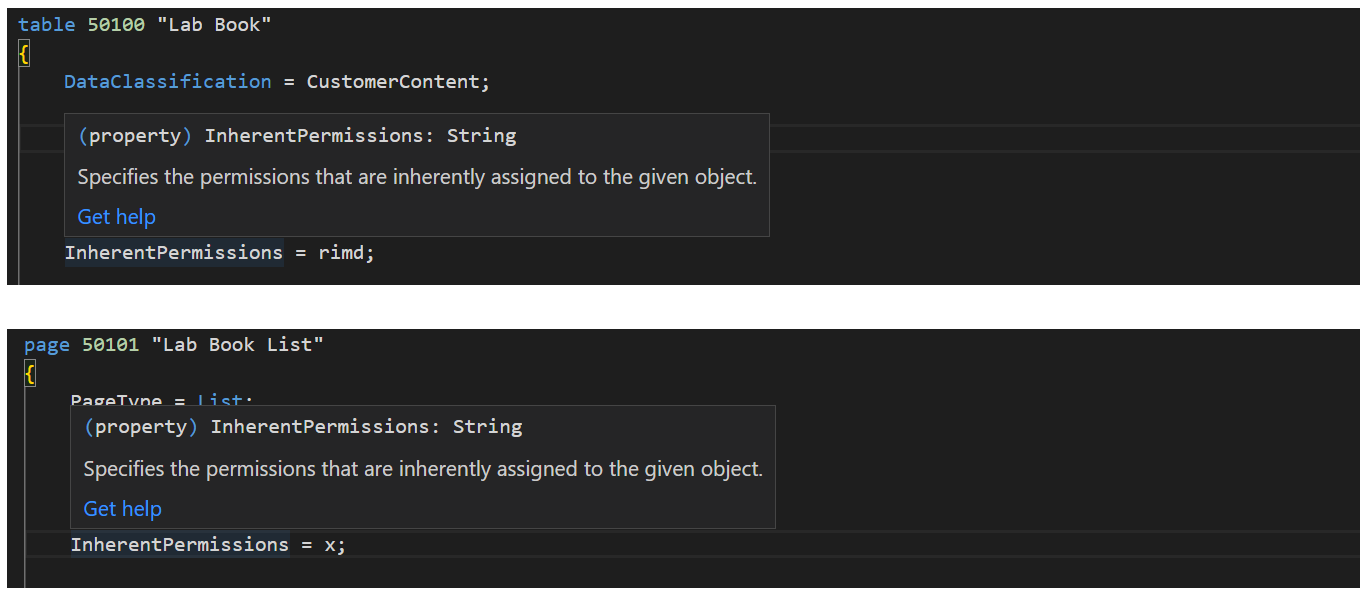
The new propertyInherentPermissionswas added to objects that can have assigned permissions. AL developers can mark an object with this property, to take it out of the permissions system.
MS Docs (Learn) has also been updated.
InherentPermissions Property: Specifies the permissions that are inherently assigned to the given object. (Version: Available or changed with runtime version 11.0)
Applies to:
- Table
- Report
- Codeunit
- Xml Port
- Page
- Query
Note
The property ‘InherentPermissions’ cannot be customized.
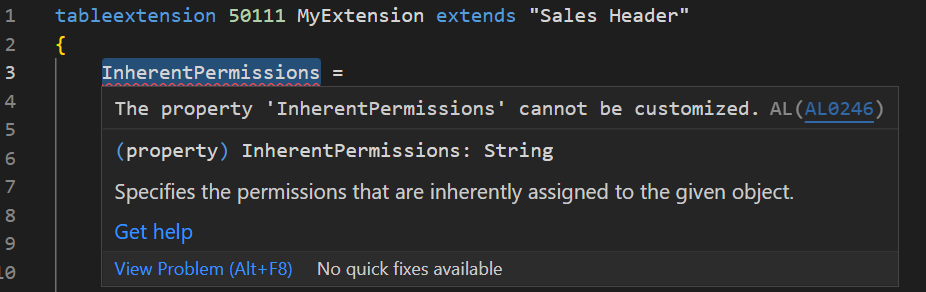
We have discussed InherentPermissions Attribute (Specifies the permissions assigned to the scope of the method) before. And InherentPermissions attribute is now available in the scope “Cloud”.
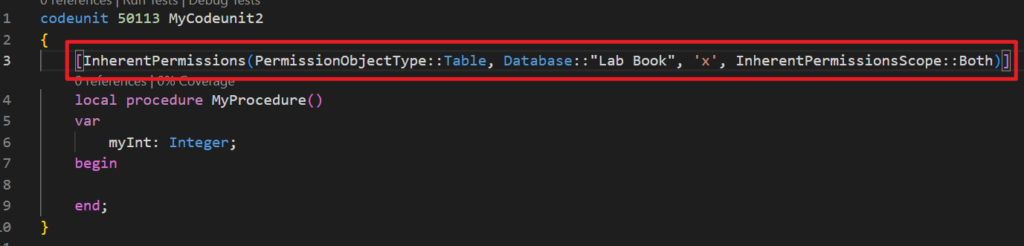
PS: InherentPermissionsScope Option Type (Version: Available or changed with runtime version 10.0.)
| Member | Description |
|---|---|
| Permissions | The Permissions scope |
| Entitlements | The Entitlements scope |
| Both | The Both scope |
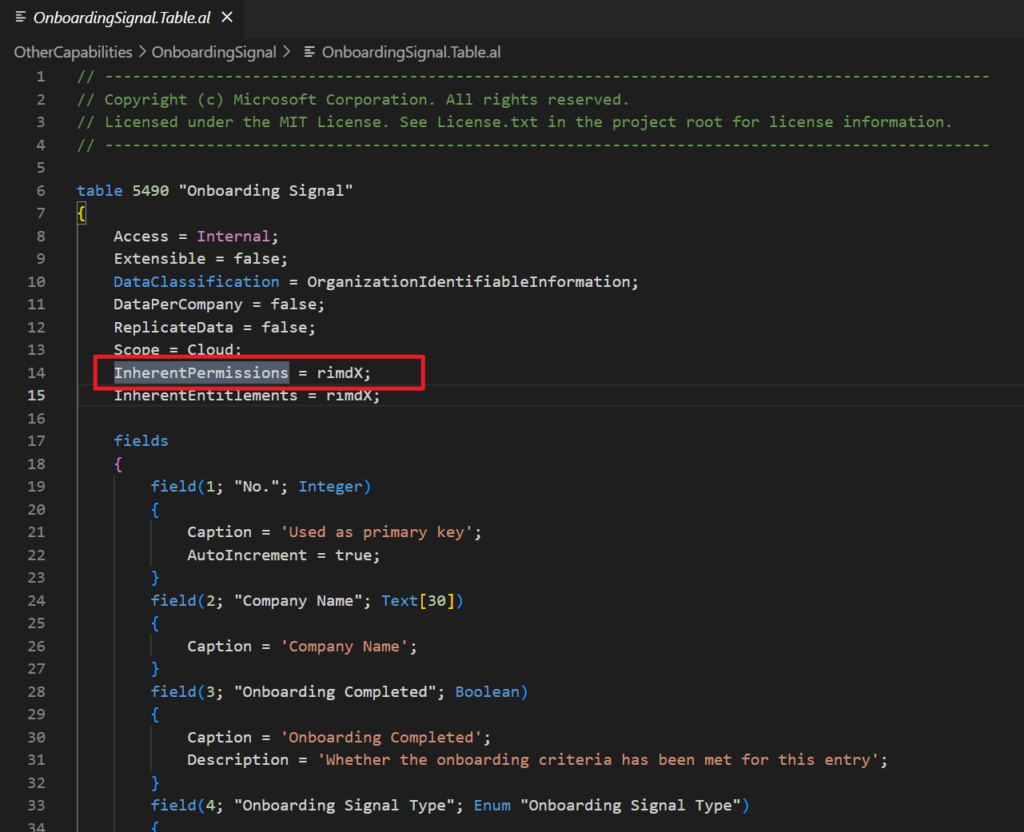
This time is another evolution of Inherent Permissions. Let’s look at the base app.
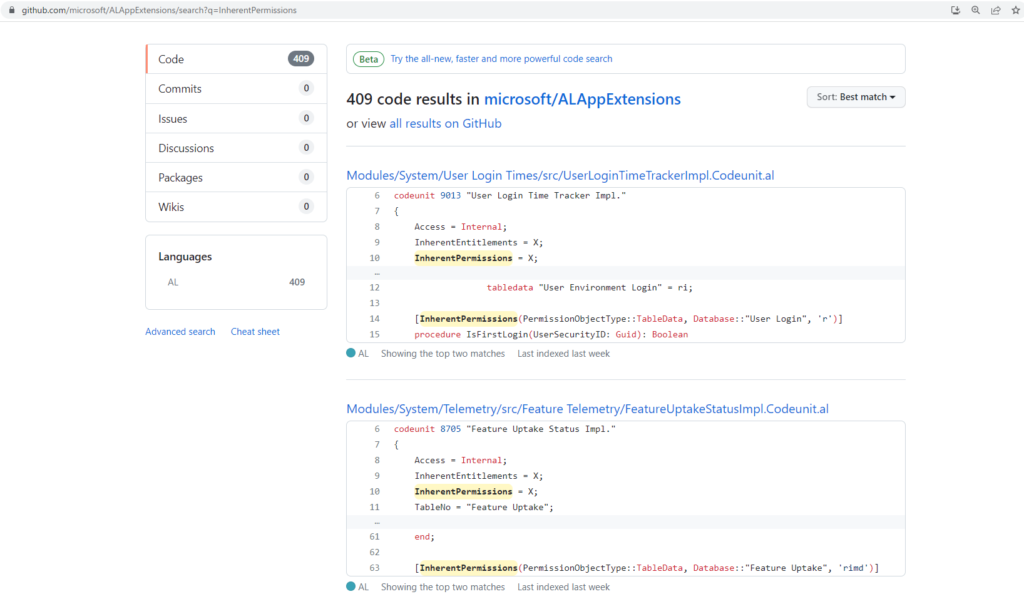
And you can find more in microsoft/ALAppExtensions.
For example, https://github.com/microsoft/ALAppExtensions/search?q=InherentPermissions
Yes, we can set the InherentPermissions Property for the our custom objects now.
The InherentPermissions Property values that are Read, Insert, Modify, Delete, and Execute are set according to the object type.
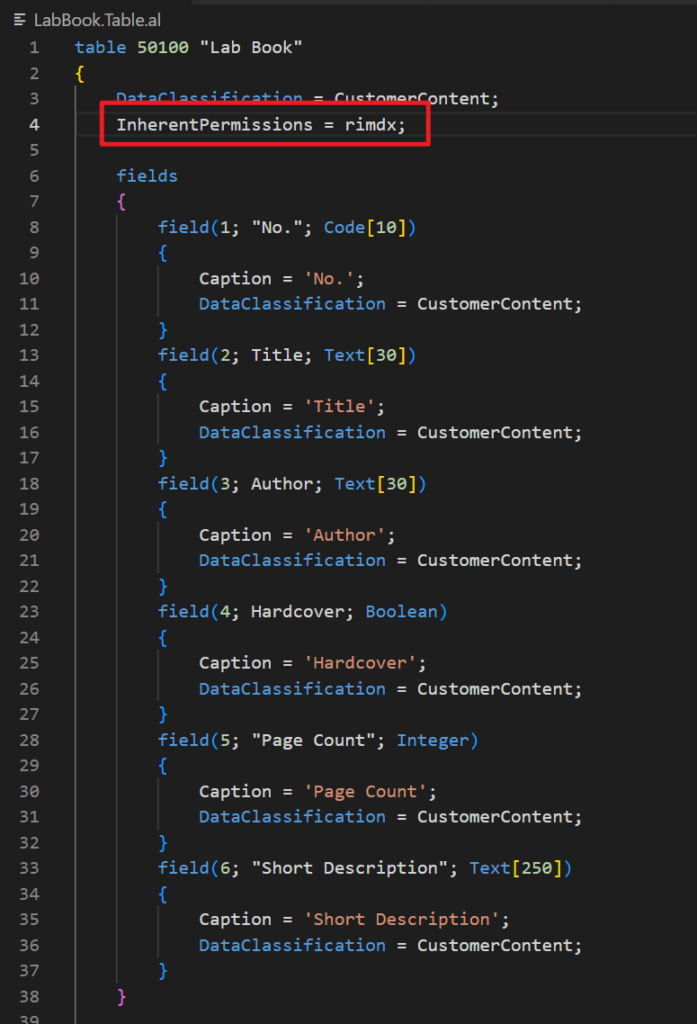
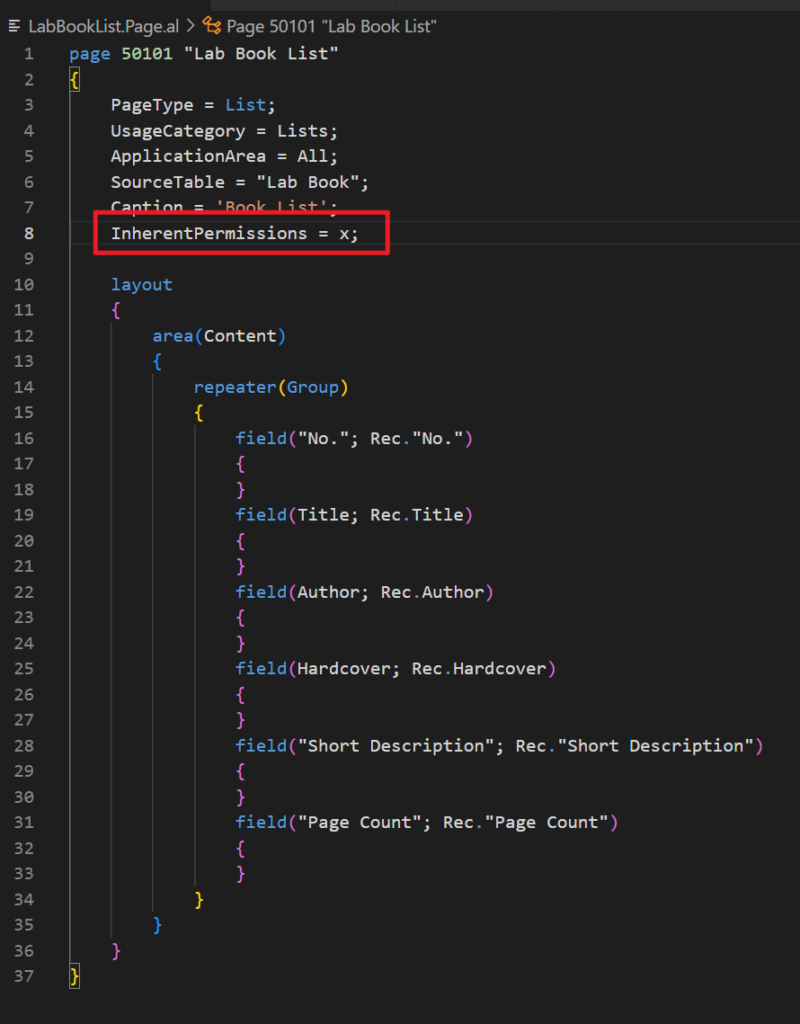
Give it a try!!!😁
PS:
1. In previous versions:
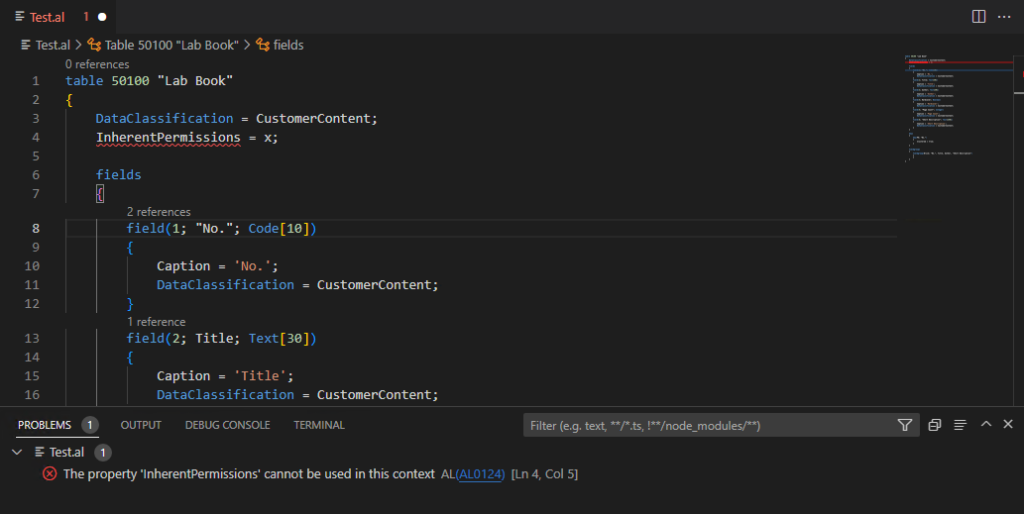
2. More details about Inherent Permissions
Inherent permissions let you reduce the number of objects that you need to control, which makes it easier to manage permissions and helps avoid permission errors.
When you’re deciding whether to use inherent permissions, consider whether you need to manage Read, Insert, Modify, Delete, and Execute permissions for the object. The following are examples of when you can or shouldn’t use indirect permissions.
Does the object run on or contain customer or business data? For example:
- Yes. The General Ledger module does contain important business data. Don’t apply inherent permissions to the module because you should control permissions for it.
- No. The Math module in the System Application doesn’t contain or run on any business data. You can apply inherent permissions to the module because you don’t need to manage permissions for it.
Is the object only run through another object that you can control permissions for? The following are some examples of when you can grant inherent permissions.
Inherent Permissions – Business Central | Microsoft Learn
- We grand indirect Read on the method scope for the General Ledger table when people sign in, because it’s only used to get the work date.
- Install and Upgrade codeunits where you can grant inherent Execute permissions.
- Buffer tables where you can typically grant indirect Read, Insert, Modify, Delete, and Execute permissions and entitlements because they’re only use to hold data in memory.
END
Hope this will help.
Thanks for reading.
ZHU


コメント