Hi, Readers.
Today I would like to talk about how to block access by location (IP Range). This was a recent discussion with a partner who wanted to prohibit users from accessing BC outside of the office.
Is this possible? Yes, of course. But strictly speaking, though, this is not a Business Central question, it’s an Azure AD management question.
This time we need to use the Azure AD Conditional Access feature (CA policies).
What is Conditional Access? (Video from MS Learn site)
Use Conditional Access policies to apply the right access controls when needed to keep your organization secure.
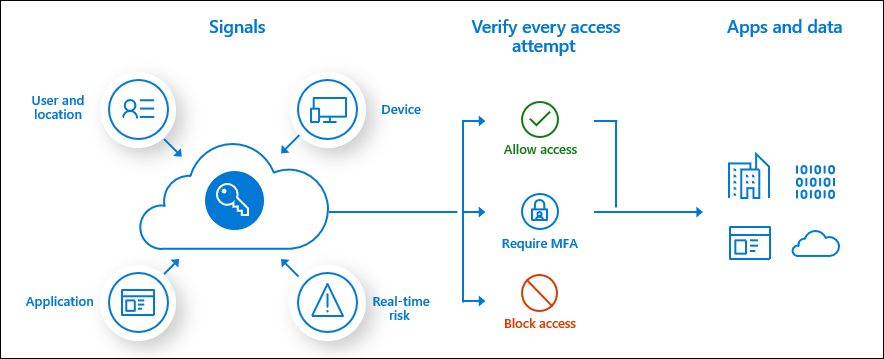
Common signals:
Common signals that Conditional Access can take in to account when making a policy decision include the following signals:
- User or group membership
- Policies can be targeted to specific users and groups giving administrators fine-grained control over access.
- IP Location information (Needed for this time)
- Organizations can create trusted IP address ranges that can be used when making policy decisions.
- Administrators can specify entire countries/regions IP ranges to block or allow traffic from.
- Device
- Users with devices of specific platforms or marked with a specific state can be used when enforcing Conditional Access policies.
- Use filters for devices to target policies to specific devices like privileged access workstations.
- Application
- Users attempting to access specific applications can trigger different Conditional Access policies.
- Real-time and calculated risk detection
- Signals integration with Azure AD Identity Protection allows Conditional Access policies to identify risky sign-in behavior. Policies can then force users to change their password, do multi-factor authentication to reduce their risk level, or block access until an administrator takes manual action.
- Microsoft Defender for Cloud Apps
PS: More MS learning modules about Conditional Access
Let’s see more details.
Block access by location: With the location condition in Conditional Access, you can control access to your cloud apps based on the network location of a user. The location condition is commonly used to block access from countries/regions where your organization knows traffic shouldn’t come from.
1. Sign in to the Azure portal as a Conditional Access Administrator, Security Administrator, or Global Administrator.
2. Browse to Azure Active Directory > Security > Conditional Access > Named locations.
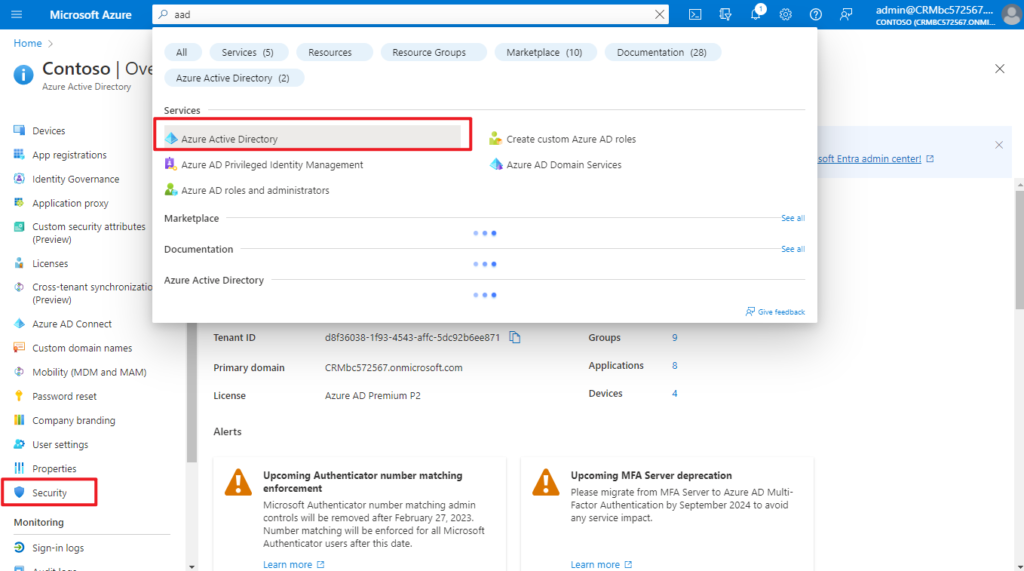
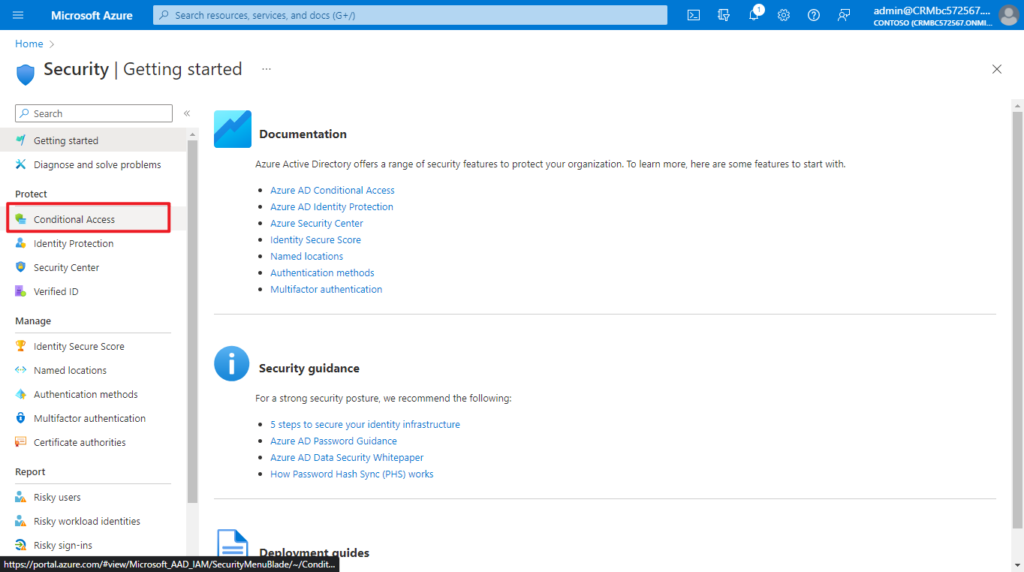
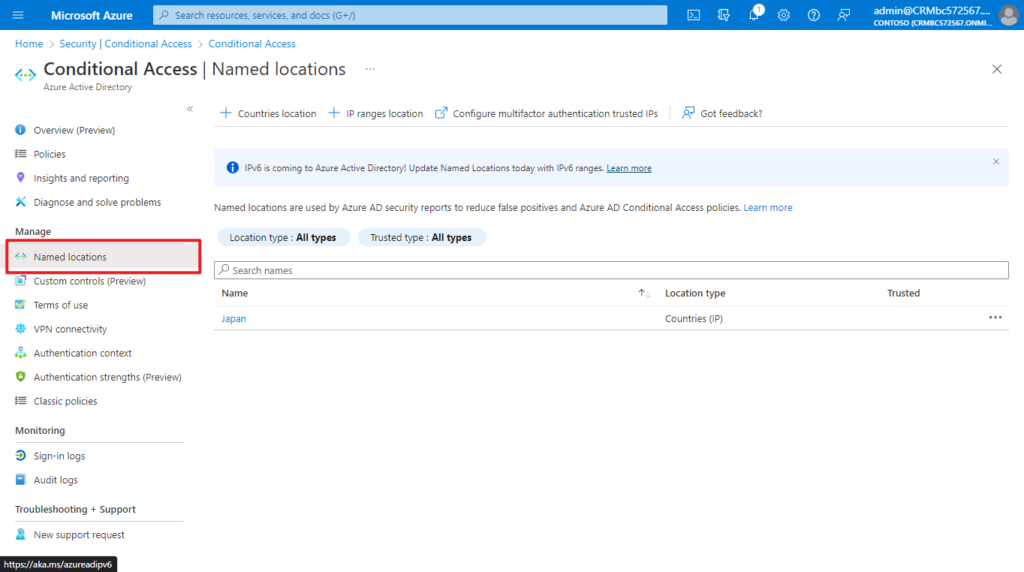
3. Add Named locations.
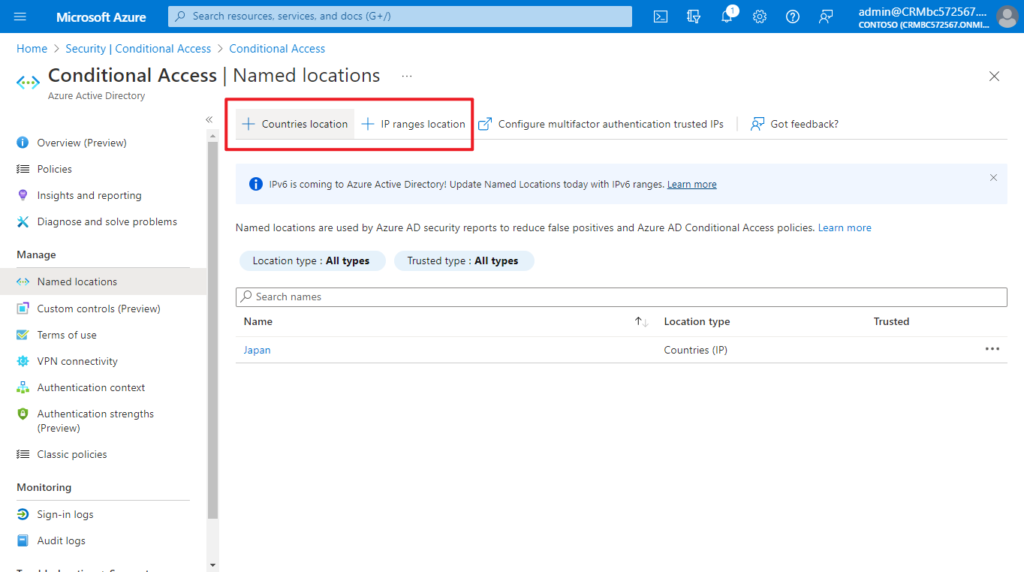
In Countries location, you can choose the countries/regions.
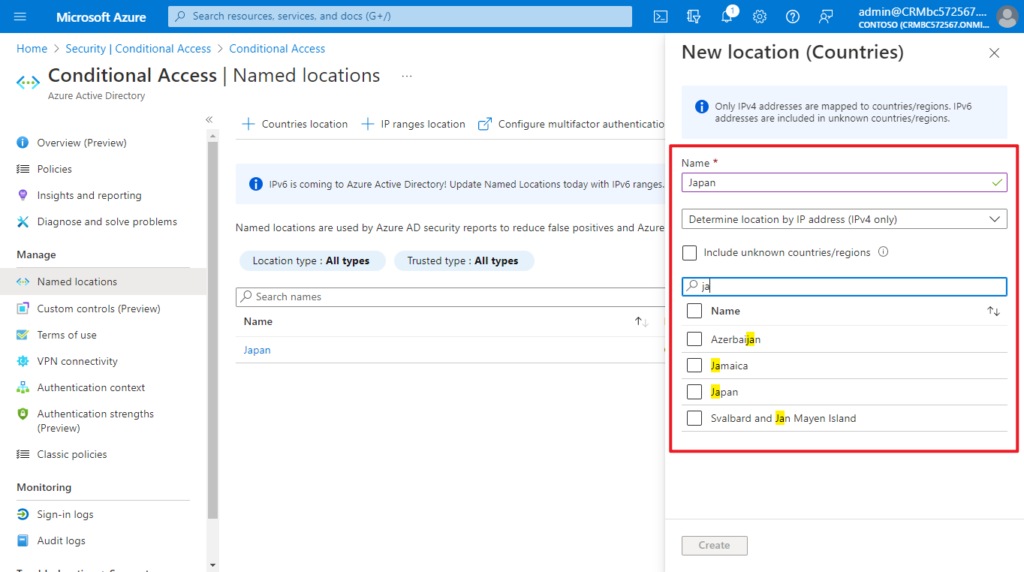
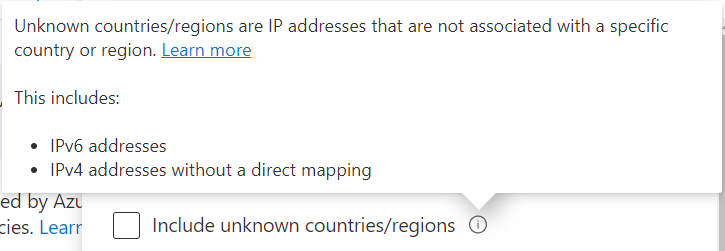
PS: Unknown countries/regions are IP addresses that are not associated with a specific country or region. Learn more
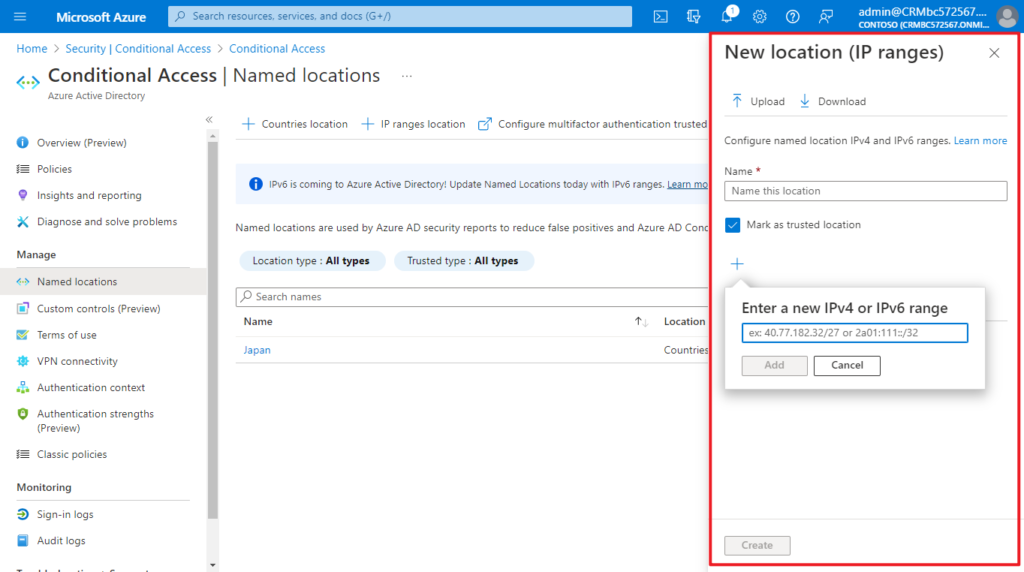
Choose IP ranges location if you know the specific externally accessible IPv4 address ranges that make up that location or Countries/Regions.
To define a named location by IPv4/IPv6 address ranges, you’ll need to provide:
- A Name for the location
- One or more IP ranges
- Optionally Mark as trusted location
Named locations defined by IPv4/IPv6 address ranges are subject to the following limitations:
- Configure up to 195 named locations
- Configure up to 2000 IP ranges per named location
- Both IPv4 and IPv6 ranges are supported
- Private IP ranges can’t be configured
- The number of IP addresses contained in a range is limited. Only CIDR masks greater than /8 are allowed when defining an IP range.
More information about the location condition in Conditional Access can be found in the article, What is the location condition in Azure Active Directory Conditional Access
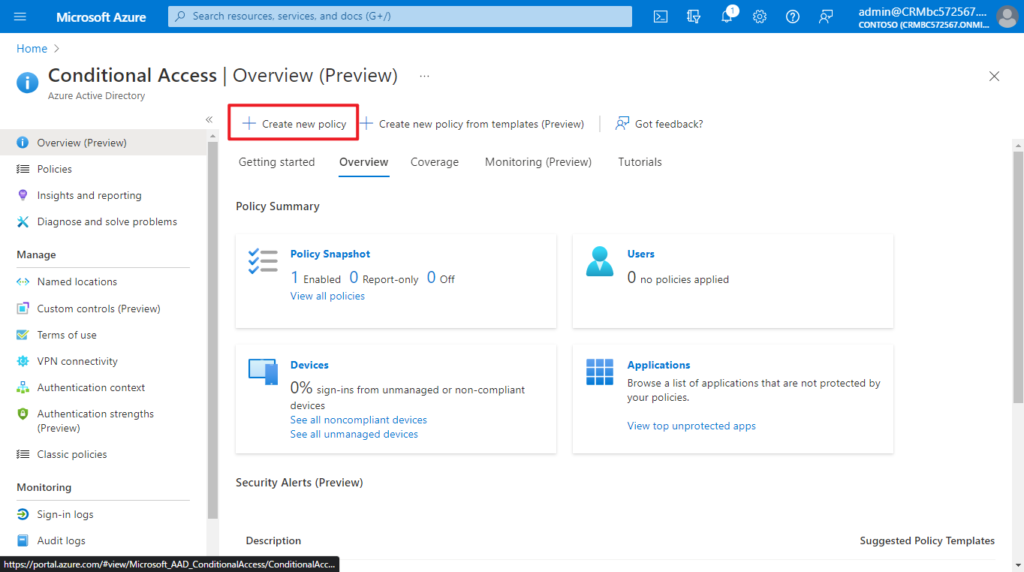
4. Sign in to the Azure portal, then Browse to Azure Active Directory > Security > Conditional Access.
5. Select Create new policy.
6. Set Conditional Access policy
(1) Give your policy a name.
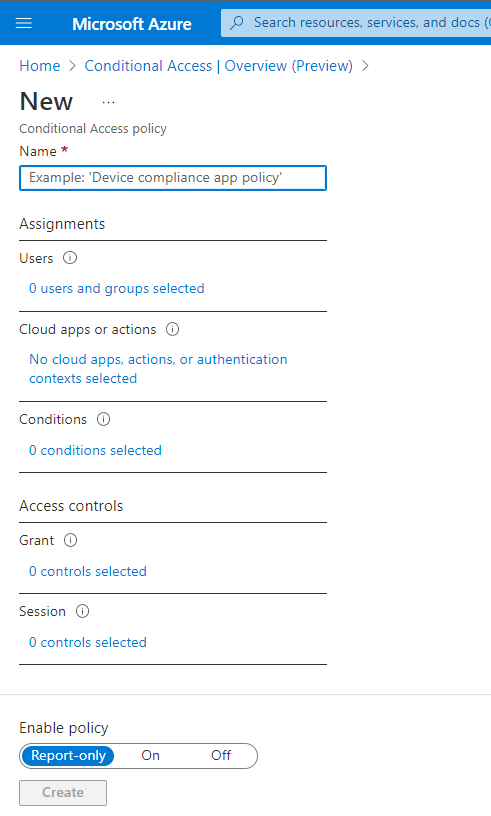
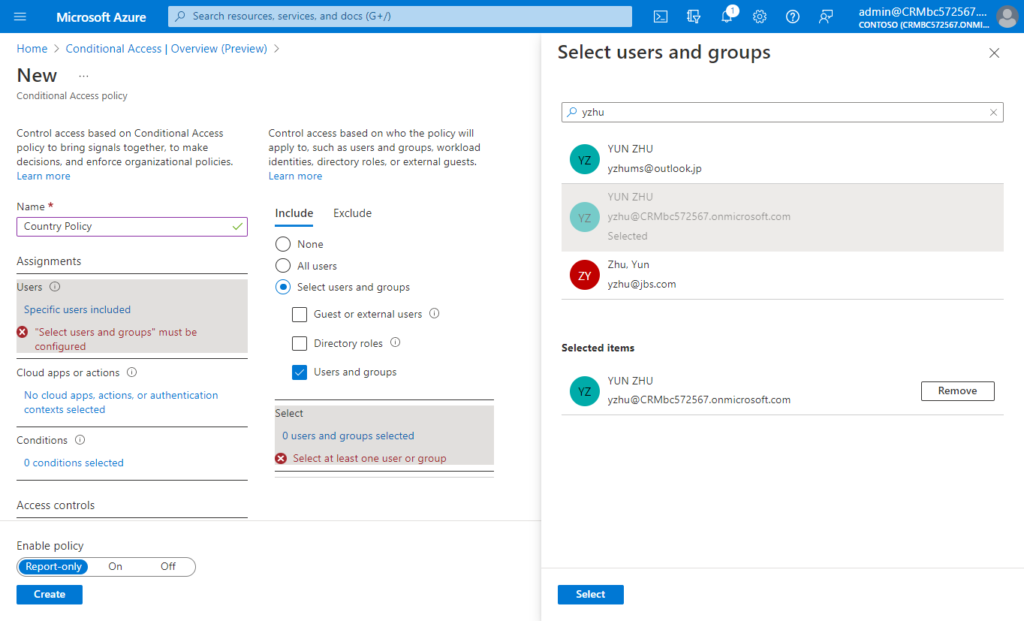
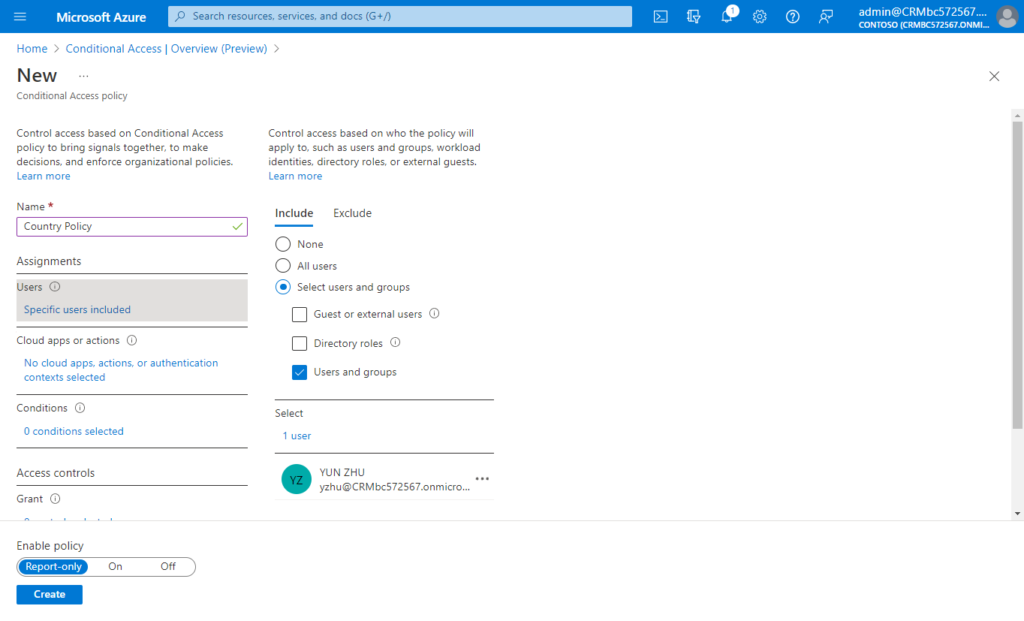
(2) Choose Users: Identities in the directory that the policy applies to, including users, groups, and service principals
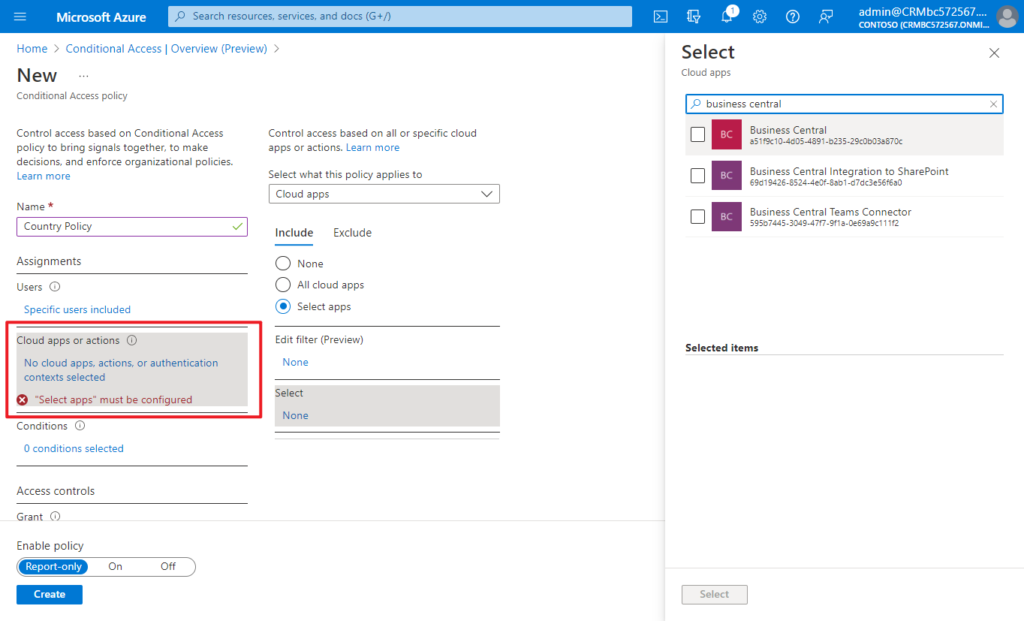
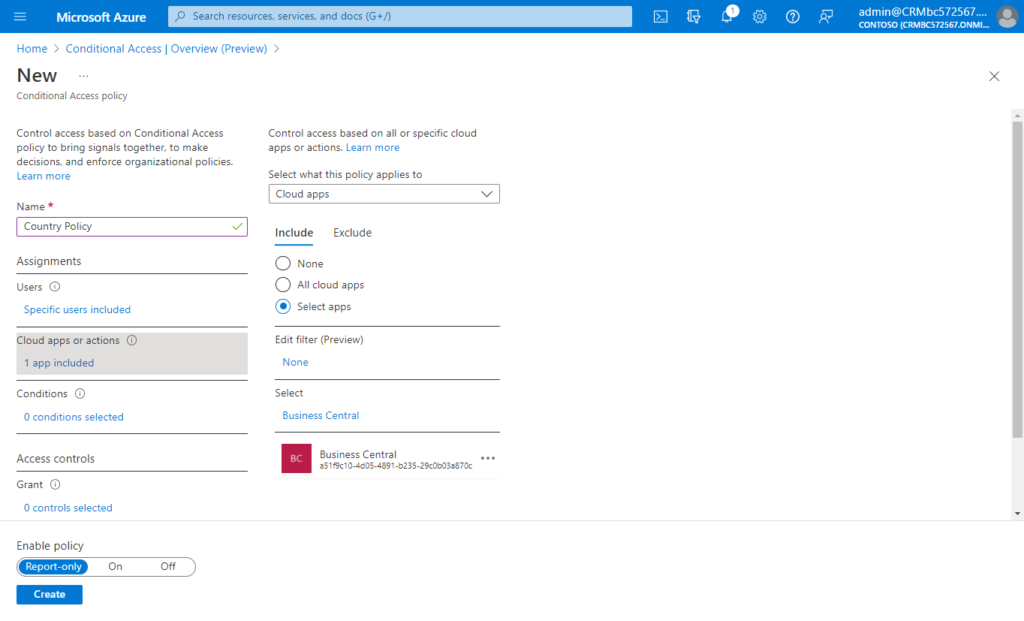
(3) Select Cloud apps or actions: Applications accessed or user actions
(4) Select Conditions: Conditions which define when the policy will apply. For example, ‘location’
- Under Conditions > Location.
- Set Configure to Yes
- Under Include, select Selected locations
- Select the blocked location you created for your organization.
- Click Select.
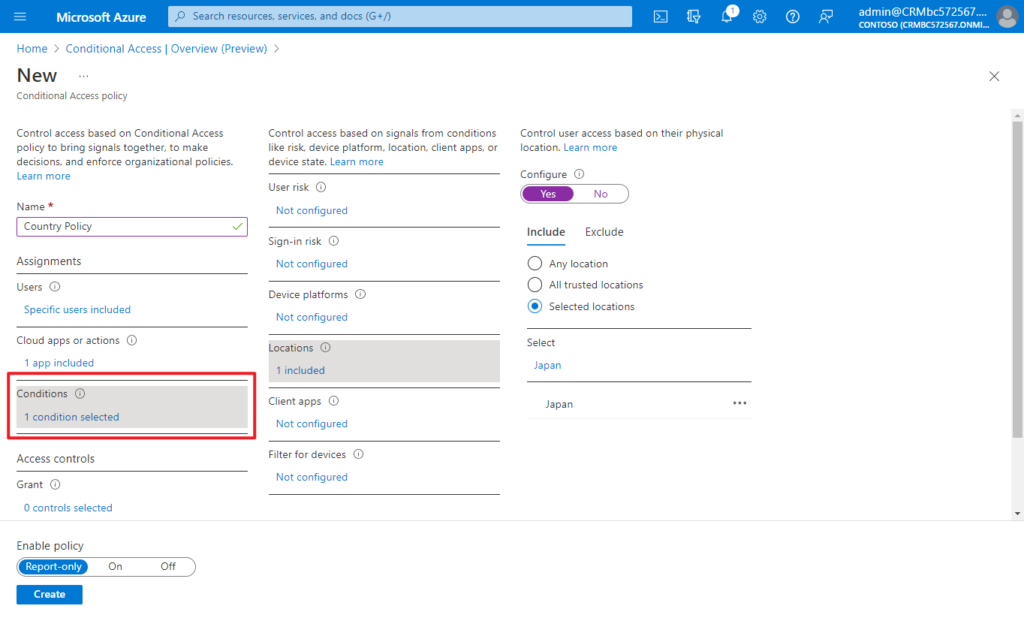
(5) Block access or select additional requirements which need to be satisfied to allow access
Under Access controls > select Block Access, and click Select.
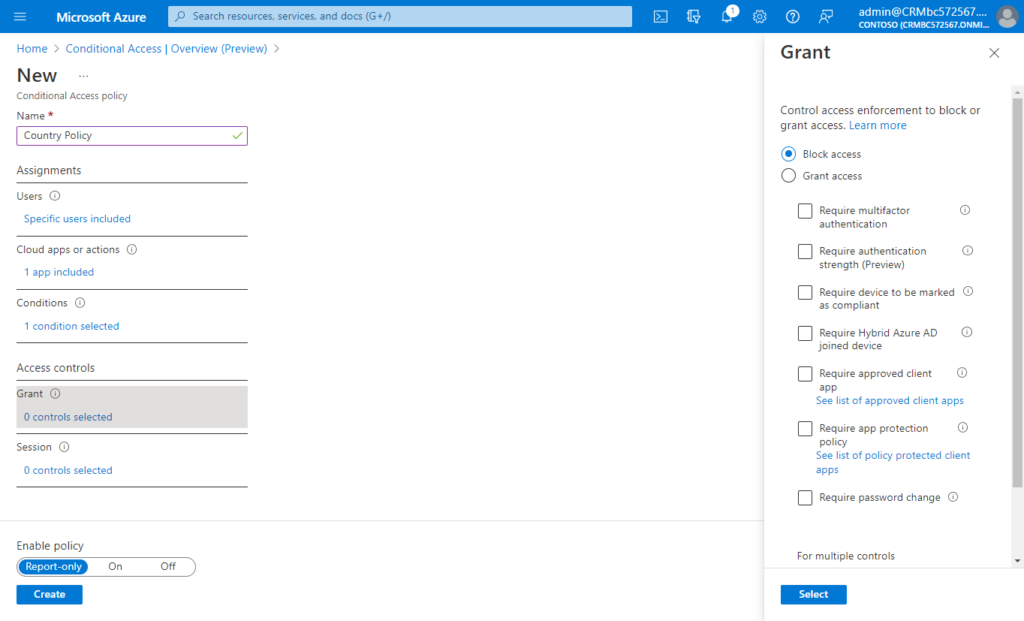
(6) Session controls enable limited experience within a cloud app: Control access based on session controls to enable limited experiences within specific cloud applications. Learn more
This time we don’t need to set.
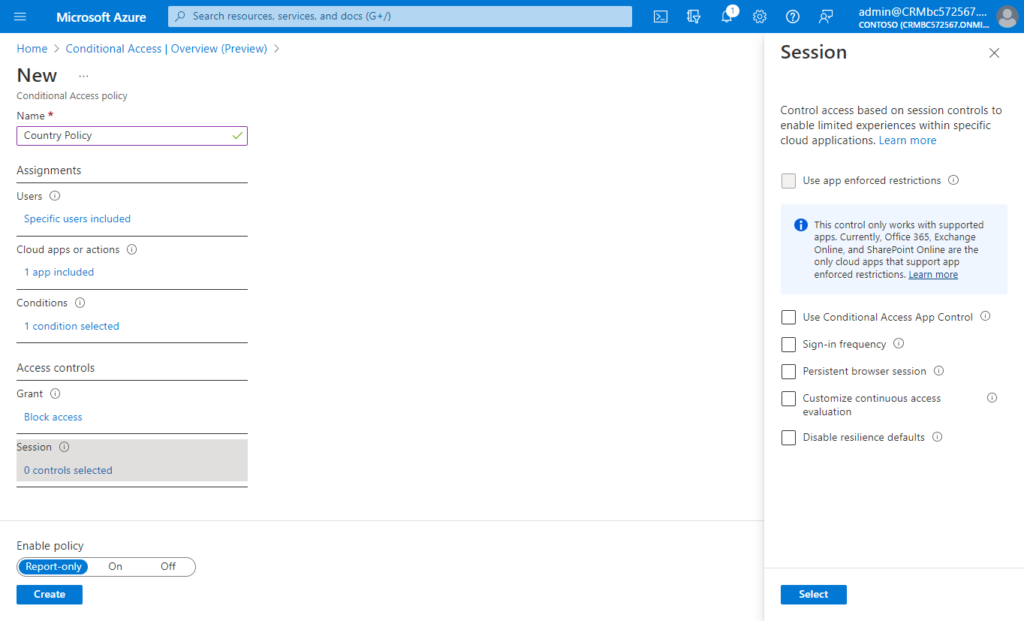
(7) Confirm your settings and set Enable policy to Report-only.
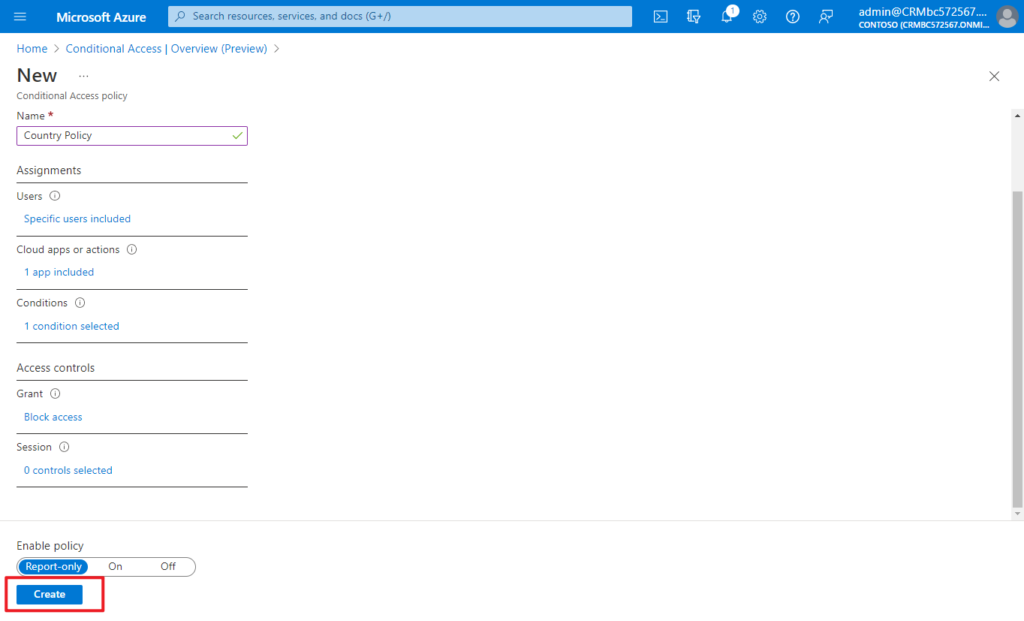
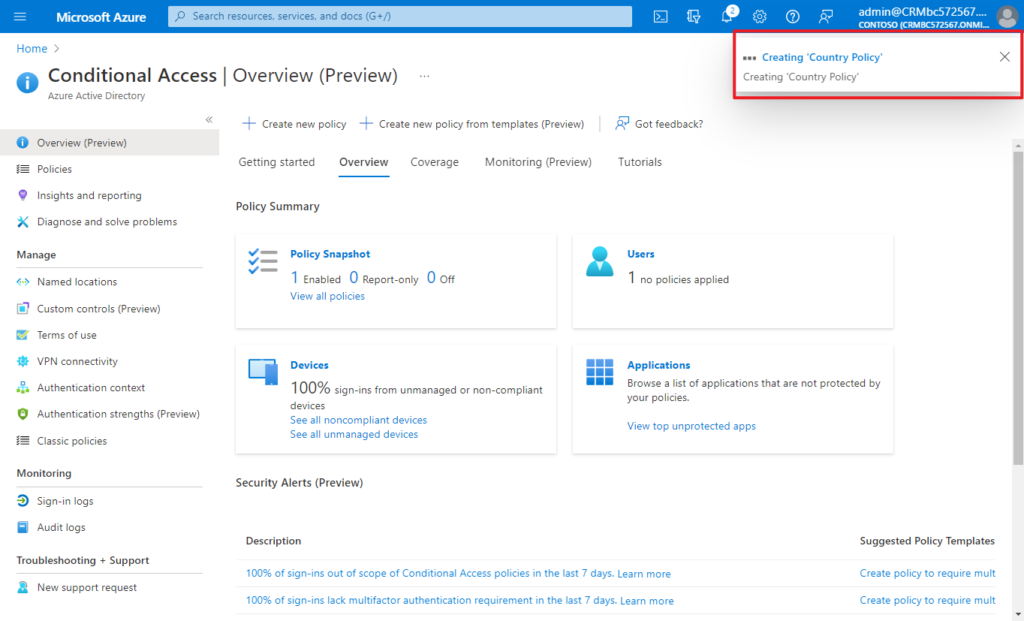
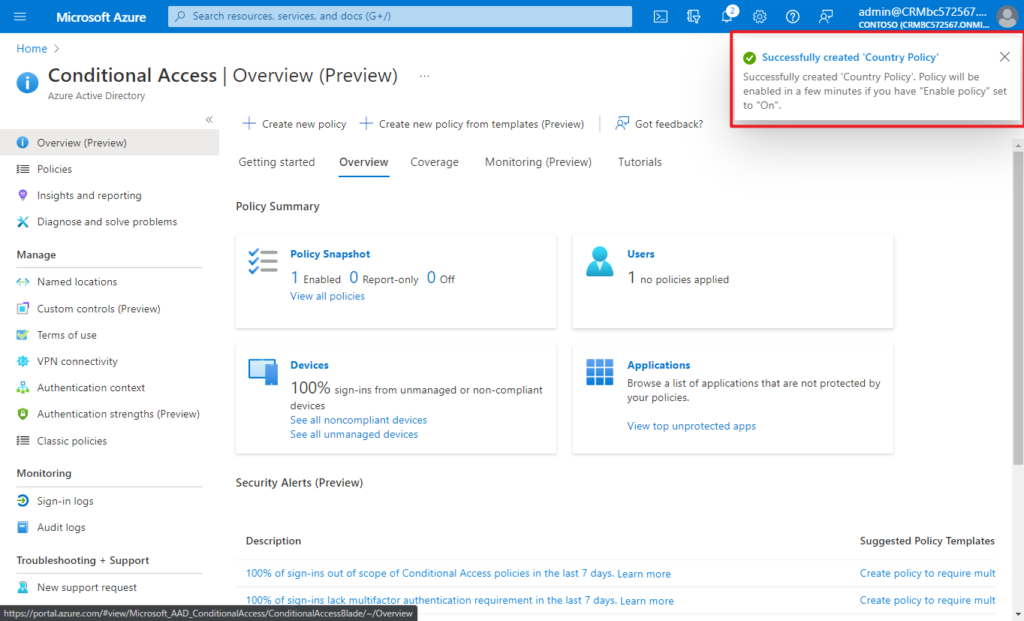
After confirming your settings using report-only mode, an administrator can move the Enable policy toggle from Report-only to On.
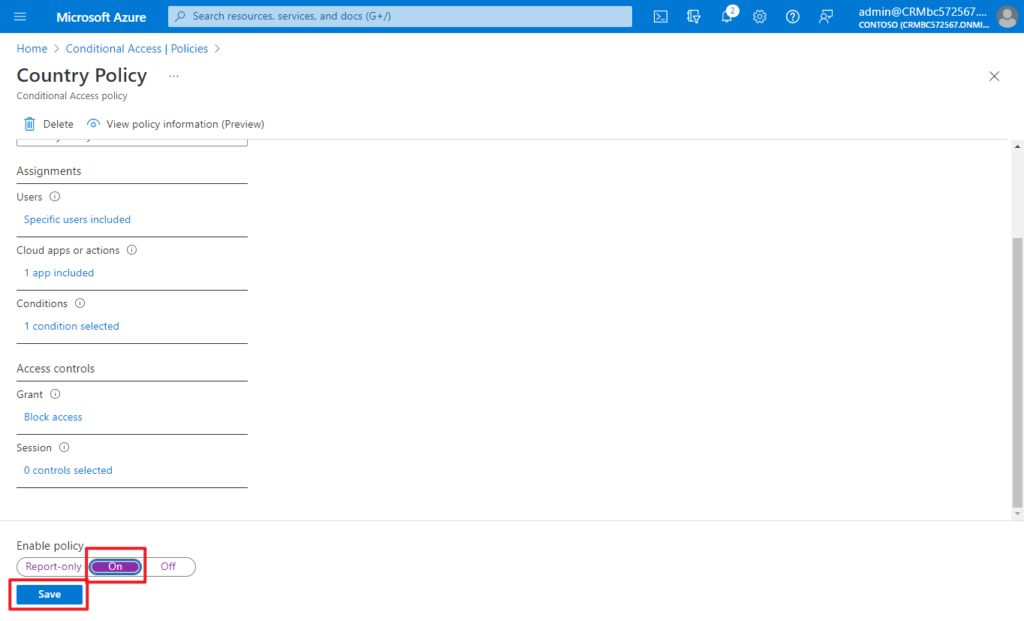
According to my test, this does not take effect immediately, and it is expected to take 10 to 30 minutes.
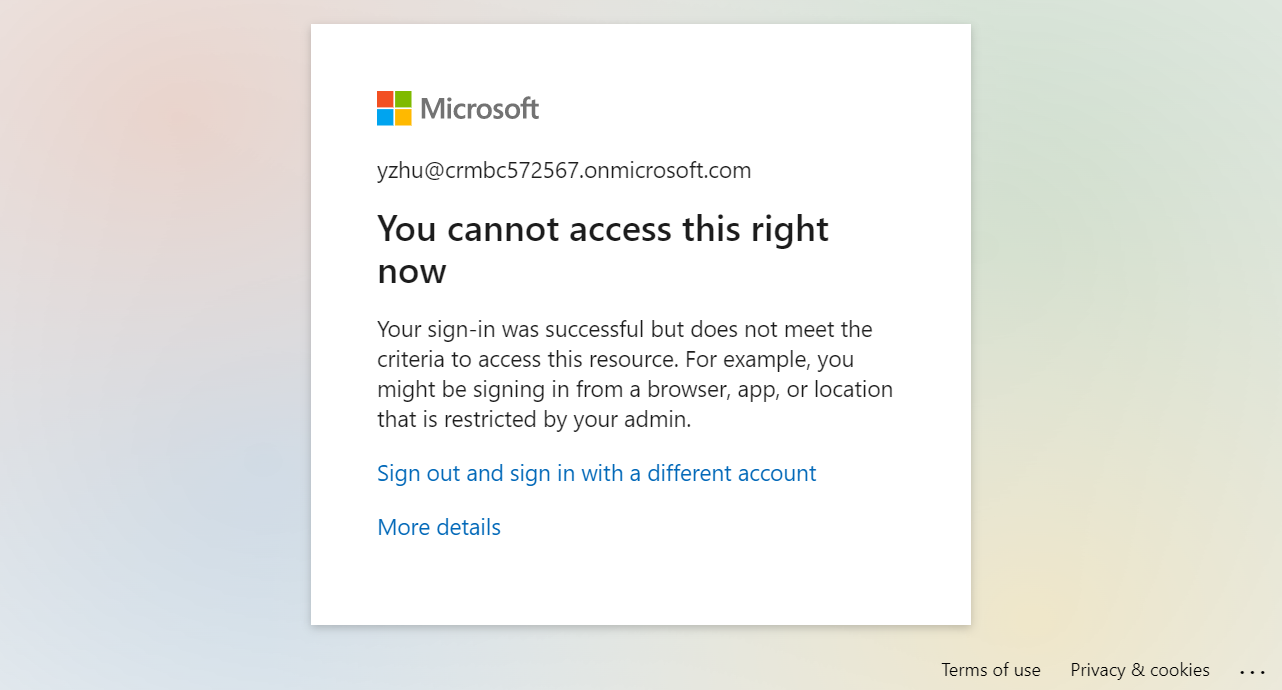
When the user meets the above CA policies, the user will not be able to access the Business Central.
You cannot access this right now
Your sign-in was successful but does not meet the criteria to access this resource. For example, you might be signing in from a browser, app, or location that is restricted by your admin.
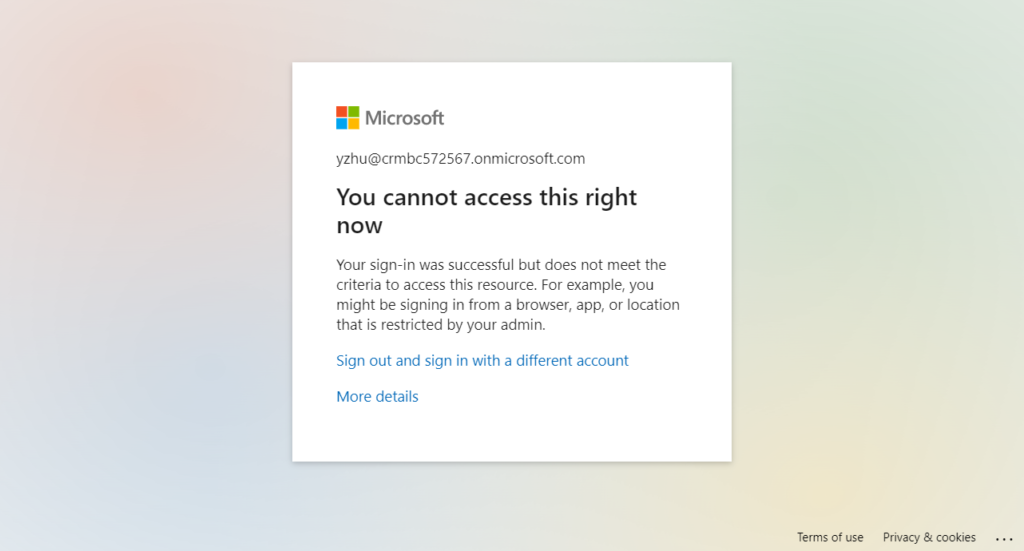
Give it a try!!!😁
PS:
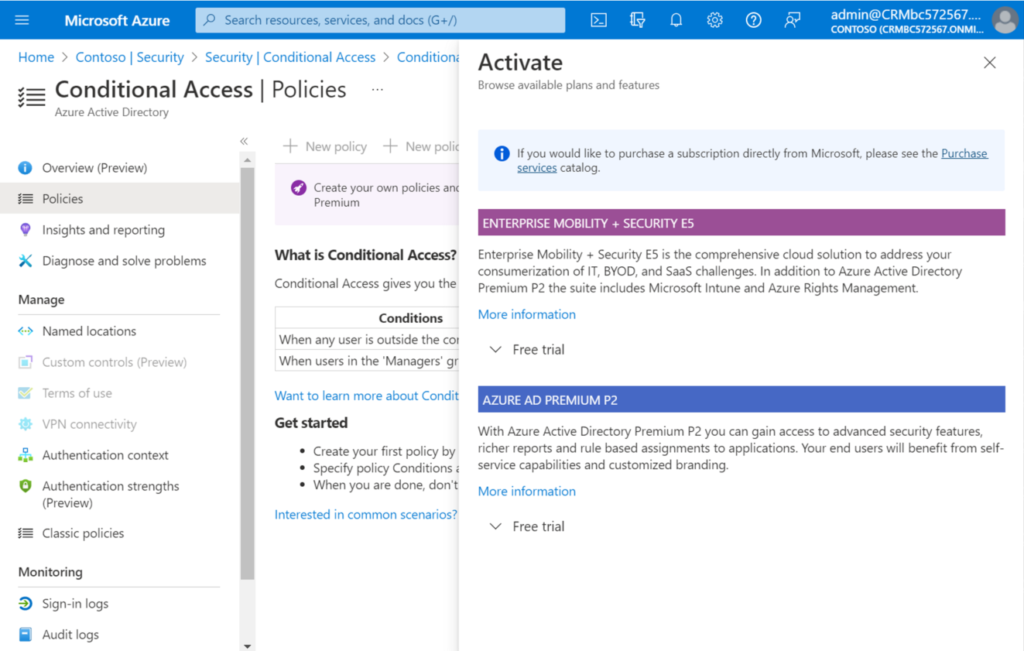
1. License requirements: Using this feature requires Azure AD Premium P1 licenses. To find the right license for your requirements, see Compare generally available features of Azure AD.
Customers with Microsoft 365 Business Premium licenses also have access to Conditional Access features.
If you don’t have a license, New policy will be greyed out.

You can test it out by requesting a free trial.
2. For APIs in Business Central: Which IP addresses or ranges does my environment’s API use?
END
Hope this will help.
Thanks for reading.
ZHU


コメント